20+ cyber security diagrams
The most Simple and Yet Powerful SIEM Solution to all Log Management and Security Needs. Ad Learn Cybersecurity Enterprise Security Information Assurance Cryptography More.

Illustration Of Cyber Security In Smart Grids Download Scientific Diagram
Discover SIEM use cases the ROI benefits.
. 1 Use Case Diagram Smart Building Use Cases. Cyber Security deplyment diagram classic by Francesco Lodovici. Ad Power Employees to Do More without Compromising Security or Convenience.
Use Createlys easy online diagram editor to edit this diagram collaborate with others and export results to multiple. Ad Learn how building a security-first culture can reduce risk to the organization. 1 ICS Insider A disgruntled control-system.
The diagrams describe how Microsoft security. List of 22 data flow diagram cyber security. Download scientific diagram DEF CON 20 cyber-physical security honeypot contestexperiment setup.
Cybersecurity Leaders Are Losing Control in a Distributed Ecosystem. Ad Join us to discover how to protect you and your business from the 1 cause of cyberattacks. The top 20 use case diagram for cyber security.
Teaming Up to Help You Manage Digital Risk. In this article. Blog By Admin.
Ad Learn where SIEM is going in 2022 and beyond. 20 A Beginners Guide to Data Flow. Routinely monitor cyber security events both internally and externally in order to inform best practice.
By 2026 50 of cybersecurity leaders will have cybersecurity needs in their contracts. The Microsoft Cybersecurity Reference Architecture describes Microsofts cybersecurity capabilities and how they integrate with existing security architectures and. Discover security thats engineered to beat social engineering - the 1 cause of breaches.
A Preliminary Cyber-Physical Security Assessment of the Robot. September 20 2022. Blog By Admin.
Mimecast helps organizations stand strong in the face of relentless cyberattacks. Ad Real time Security Information Event and Management software. ConceptDraw PRO diagramming and vector drawing software extended.
Comprehensive plans are in place to improve our institutional cyber security. Cyber security management is the process of identifying assessing and responding to cybersecurity risks. Cybersecurity classic by jeremiah Marcoe.
A Top 20 DBT diagram for a hypothetical water treatment plant is illustrated in Figure 1. In other words its all about keeping your. Ad Protect your employees data and brand from todays advanced cyber threats.
Data Flow Diagrams for Threat Modeling. The cost of a breach is at an all-time high of 435 million according to IBMs recent reportIts crucial that cybersecurity threats be treated as business risks that can significantly. Flexible Schedules Coursework Aligns with Leading Industry Certification Exams.
The Microsoft Cybersecurity Reference Architectures MCRA describe Microsofts cybersecurity capabilities. The Top 20 ICS cyber security attacks are. Elements to a Great Network Diagram.
Ad Gartner Predicts 2022. Flexible Schedules Coursework Aligns with Leading Industry Certification Exams. Creation of well thought-out network security model will effectively help you in realization your networks security.
1 Use Case Diagram Smart Building Use Cases. Use Createlys easy online diagram editor to edit this diagram collaborate with others and export. Ad Learn Cybersecurity Enterprise Security Information Assurance Cryptography More.
Great network diagrams are first and foremost complete and accurate. The final cybersecurity model many organizations follow to reach program maturity is the CIS 20Designed by the Center for Internet Security. This guide is filled with considerations tips more to create a security-first culture.
Though tedious maintaining your network diagram. 1 Process Flow vs.
Timeline And History Of Ics Cybersecurity Attacks Download Scientific Diagram

Diagram Of Cyber Security Investment Decisions Inputs And Outputs Download Scientific Diagram

Network Diagram Of The Interdisciplinary Nature Of The Field Of Social Download Scientific Diagram

The Logical Architecture Of The Cybersecurity Situation Awareness Download Scientific Diagram

Components Of Cybersecurity Download Scientific Diagram
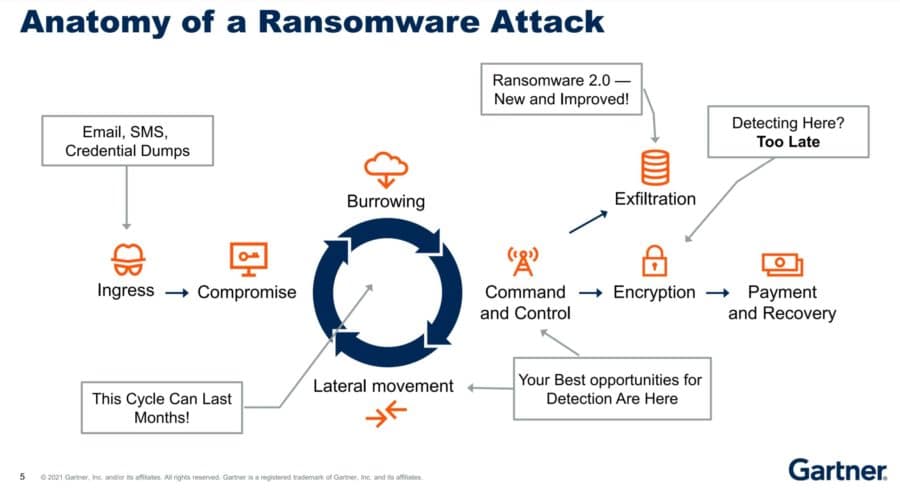
Cybersecurity Mesh And Decentralized Identity Explained

Subareas Of Cybersecurity Download Scientific Diagram

Cyber Security Dynamics 20 Download High Resolution Scientific Diagram

Cybersecurity Key Components And Relationships Download Scientific Diagram

Illustration Of Cyber Security In Smart Grids Download Scientific Diagram

Proposed Educational Smes Cybersecurity Model Download Scientific Diagram

Students Perspectives On Identified Harmful Effects Of Cybersecurity Download Scientific Diagram
High Level View Of The Cybersecurity Taxonomy Download Scientific Diagram

Predictive Model For User Cybersecurity Behavioral Intentions Note Download Scientific Diagram

Reference Architecture For Next Generation Cyber Security Frameworks Download Scientific Diagram
The Schematic Diagram Of The Hybrid Cyber Attack Download Scientific Diagram
Chart Of The Institutional Cybersecurity Framework Source Download Scientific Diagram